The article discuss general security issues in organizations by considering some common security components.
Introduction
In order to run a business smoothly and continuously without interruption it is very important to manage company’s day to day security functions. To do that it is needed to place correct procedures and process relevant to security operations.
Security operations management is the ground process by where manage security incidents of an organization and report and communicate those events effectively. Also this covers placing proper controls to avoid security attacks and continually monitoring security functions of the organization. Forensic analysis is other important part of these operations and it focuses to properly collecting evidence of security related incidents and analyze those in a standard way.
Business continuity planning and disaster recovery is another important thing to consider for smooth operations in an organization. This is covering how to react for unexpected disasters like floods, earth quake etc. The goal of disaster recovery is to take the system into operation level after a disaster.
Physical security is another important factor in security operations and under this we discuss about security of buildings, computer equipment, documents, site location, accessibility and lighting etc.
Authentication and Authorization controls who can access the computer resources and level of the accessibility of those recourses.

Details
Security Operations
Administrative abuse of privileges. –System administrators make sure systems running smoothly, Provide an assurance to integrity and availability of computer systems. in Order to do this normally System administrators have more privileges than ordinary users. Sometimes administrators might abuse their rights, unauthorized use of systems services and data. To avoid administrator abuse of computer systems we have to put some controls over administrative privileges.
To avoid administrative abuse of power we can limit authority and separate duties. Within our IT Infrastructure We can segment system operations to different authority and assign separate administrator for each Job. Also we can segment duties based on service administration and data administration.
System changes such as updates, patches, new releases, and configuration changes might cause unexpected issues and make system unavailable. in order to avoid these kind of situations practicing a proper change management process is very important. Normally before implement a change, It is very important to do an impact analyze of the required change. also recording the change and testing before apply to the production environment is very important.
ITIL provides a service oriented framework, a set of best practices for properly manage the changes specially for service oriented organizations learn more.
Disaster Recovery and Business Continuity
Issues with third party vendors- Most of the organizations outsource some of their business operations /Management operations with third party vendors. Examples of outsource operations are, virtual servers, Internet service providers, Payment Systems, Backup servers etc.
If we plan our disaster recovery and business continuity plans without involving our third-party vendors and service providers those would not success. Because those vendor involvement are part of our business operations and their contribution in disaster recovery and business continuity planning is very important. So when we preparing business continuity and disaster recovery plans, we should discuss with our third-party vendors and make sure their availability and on time contribution.
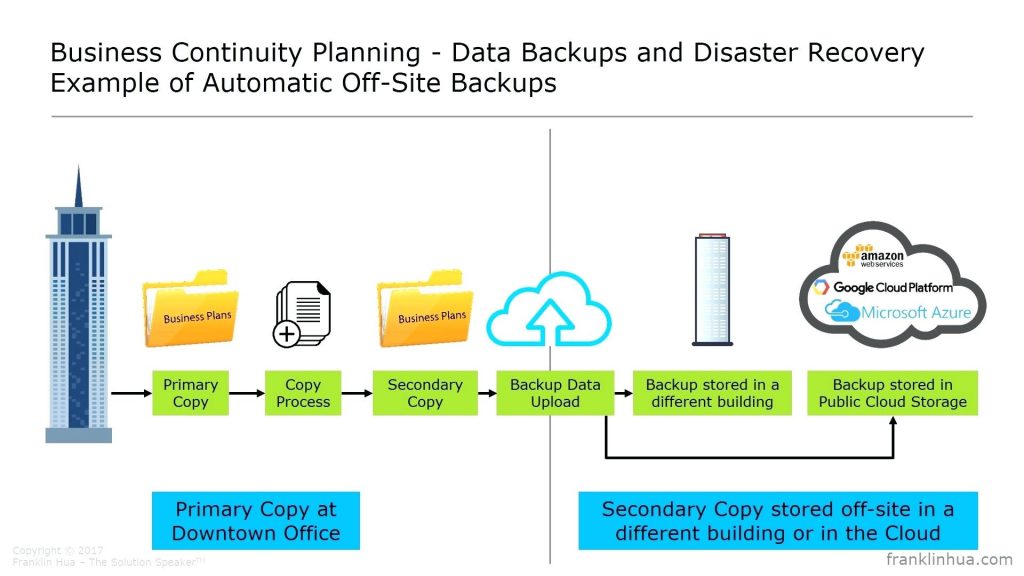
Issues of taking backups of transactional processing systems having high volumes of transactions – Using traditional online and offline backup methods can make some performance issues in high volume transactional processing systems. In order to overcome this kind of issues there are some new backup technologies to use and below list shows some of those.
Incident Response and Forensic Analysis
There are some organizations, they face the same security breach incidents again and again. Although the organization has an incident response team and quickly solve and response to incidents, the organization experience the same type of attacks regularly. The reason might be the organization do not has a proper incident management plans and procedures to manage incidents.
Physical Security
Insider security threats – Most of the organizations make necessary controls over physical security threats and do not concern about insider security threats. But this is a very important factor to consider on physical security controls. Most of the organization use temporary contracted employees for their work. Also system administrators have more power than regular users. Most of the times organization came a cross situations like stolen of removable Medias by their employees. Also contracted employees can keep malware and backdoors when they leave from the organization. To overcome this kind of issues following controls are very important
Conclusion
First section of the article shows a typical network diagram with most commonly used network components and interconnection between those components. Also the diagram shows multiple branches and connection points to internet. In addition to those the diagram show network security related devices and components like firewalls, IDS/IPS etc.

Next section discuss issues relevant to security operations. The document focus on the following areas and discuss two issues in each area.
- Security Operations
- Disaster Recovery and Business Continuity
- Incident Response and Forensic Analysis
- Physical Security
- Security Organization
- Authentication and Authorization
In addition to the issues in above areas, the document described possible solutions and suggestions to overcome those issues.
